SSL v3 (POODLE) n Heartbleed Vulnerability
Posted under » Ubuntu » Apache » LAMP Security on 15 October 2014
New SSLv3 bug aka POODLE will disable ssl v3 in our webservers
Relevant config changes in apache (either in http.conf or ssl.conf) to disable SSLv3 and weak ciphers
In Ubuntu 14.04 or 16 it the conf. is enabled as a mod. It is found under /etc/apache2/mods-available/. So be careful when you update your apache. This file might be overwritten to the default.
Update 2016. TLS 1.0 is now considered vulnerable. SSL v2 is no longer in use.
SSLProtocol all -SSLv3 -TLSv1 SSLHonorCipherOrder On SSLCipherSuite ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS
For added measure, read only your SSL certs.
chmod 400 anoneh_com.key
Once done.. service apache2 restart.
To confirm everything is in order, user the NMAP tool.
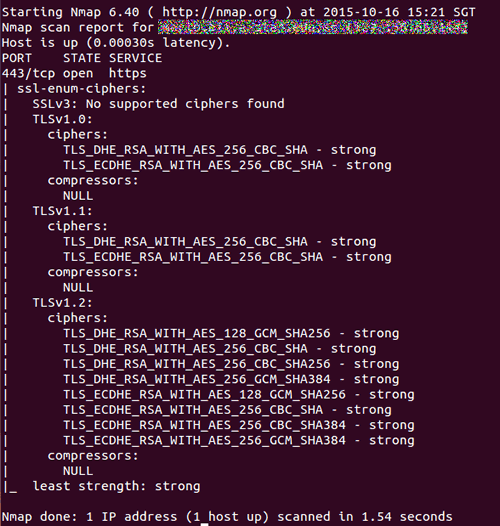
TLS 1.0 and SSLv3 are old technologies which is to there for backward compatible sake but very insecure. TLS 1.2 has backward compatibility so you don't need the old ones.
If you do not wish to install NMAP, you can use the online tool Qualys.
For heartbleed, there are sites like https://filippo.io/Heartbleed/


